Despite the impressive prophecies about the imminent disappearance of GSM, it continues to exist and develop.
The high level of mobile penetration, tremendous growth rates of mobile devices, and high margins for operators of services, convenience and reliability for customers made mobile communication an integral part of our lives, including business life. Daily millions minutes of business negotiation go through the GSM network. Most often, everything goes well, but you should not forget about existing threats in the networks.
We should start with the fact that the full security within the GSM - is a myth. Those who are trying to say the opposite, simply mislead people, and sometimes are scams. Modern technologies allow to cope quite well with existing encryption algorithms and protection mechanisms in the network GSM.
The company Tottoli GSM is not an expert-theoretician, who simulates the threats and seeks for ideal solutions "in a vacuum". Tottoli GSM is a company with practical experience in developing solutions for SIM-cards and this article - a dry residue of many years of practical experience. There are many materials related to the demonstration of interception GSM signal, remote SIM-cards hacking and some other. But here it is necessary to take into account that all these stories took place in the laboratory or in specific circumstances, or with the use of the super-expensive equipment. We talk about daily practice of communication of subscribers and protection of their privacy from intrusion by taking the fact that nobody can guarantee 100% protection. At the same time, our technology can make a secure connection on a high level. Our task is to tell about threats and possible methods of protection, the security of your communication is your own decision.
LESS – Law Enforcement Support System – a system of technical means for conducting Operational-Investigative works. Frankly speaking, it forced evil prescribed by law in some countries, which obliges operators to introduce the system for controlling its subscribers. Otherwise the mobile operator may be deprived of license.
From an engineering standpoint LESS is a control panel (CP), which allows to send commands to the network and receive responses and data for these requests. With the development of mobile and converged networks, as well as the provision of text, voice and Internet services in GSM, LESS experienced modernization and became a serious hardware-software system, without losing its original logic. In addition to the usual components there are special mediators, which are designed to process and transmit the information to a LESS CP.
In fact, LESS CP became high loaded distributed information center - because its task is to process huge amounts of information flowing through the channels as a multiservice traffic (voice, e-mail, data and so on. - it is not even worth talking about diversity of traffic in the networks of new generation NGN).
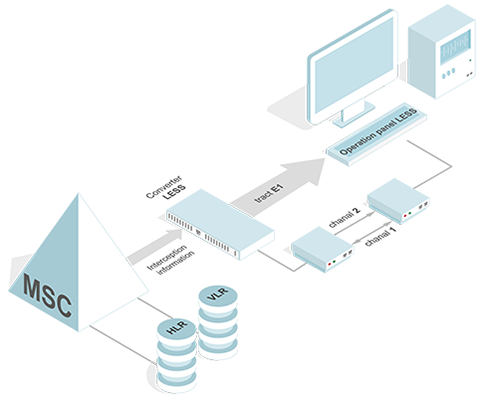
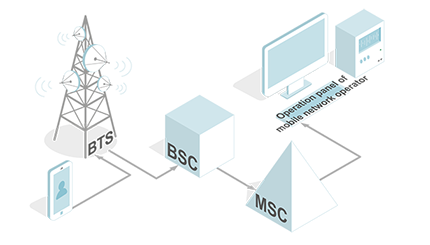
Practical implementation of lawful interception is not anything extraordinary, and is provided through interaction with the operator's network components. Interception management function solves the problem of ensuring the formation of the network of points of interception and the task of supporting of receiving the information of interception. Further, information is transmitted via specific protocols to the LESS control panel of agent concerned.
The mobile operator keeps the full information about subscribers. And it comes from two sources: from the subscriber registration form (personal data) and information transmitted to the billing while using the services.
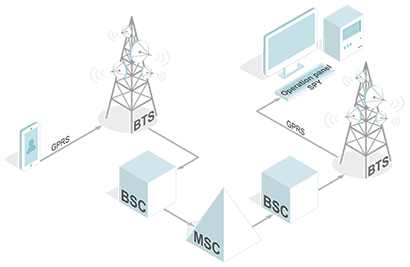
The network subscriber identification module is a SIM-card, which has a number of parameters and in conjunction with the special settings of the mobile device can tell everything about the subscriber. So, in the database of the billing system certain information is loaded: call logs (direction, number, duration), geo-targeting (determined by binding to a base station and a cell), the volume and usage profile of traffic, SMS, MMS and so on ... Of course, the operator is taking unprecedented measures to protect this information, but leaks happen, and public become aware of many of them.
Besides the threat of compromising billing, the danger can come from the services of the network provider. So, innocent parental control service or any tracking service can be perfectly used to track the movement of the subscriber.
Many of us have heard about the spy scandal, spyware and wiretapping, which we get once we buy a cell phone.
Indeed, today's devices are extremely flexible in configuring various tracking systems, and it is connected with the fact that there are a lot of software on a device, even operating systems. Hardly anyone would argue that writing a program and implementing it in the logic of the operating system is much easier than looking for ways to intercept data on a physical level. An additional threat is created by a continuous connection of devices to the Internet and transfer of geo-targeting tags. And, of course, will not be superfluous to remember that the director of the company may be presented a brand new phone, which simply has special program installed and ready to collect the necessary data.
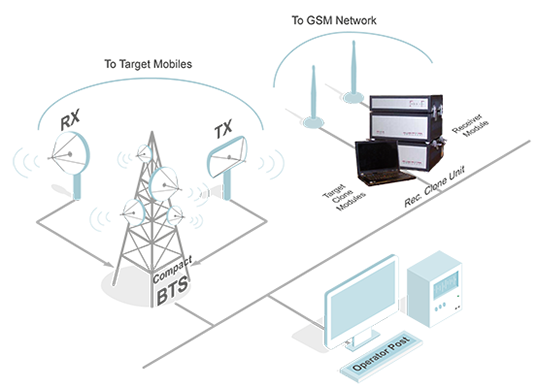
(Intercept complexes: active, semi-active, passive and other interceptors)
Perhaps, it is the most interesting source of danger in the style of techno-thriller. In the cellular network systems of the first generation maintaining the confidentiality of the conversation was a difficult problem to be solved – due to the analog origin of the voice signal, interception could be implemented by a quite simple device. In modern systems it is incomparably easier to protect the conversation - thanks to digitization. Within digital encoding, analog voice is converted into a stream of binary data to be encrypted, scrambled, and so on ... However, there is an incredible number of ways to capture traffic on the "physical" level. We tell you about some of them.
A false base station (IMSI catcher), which lowers the specified in the network encryption level and makes data interception easier. It works with a unique identifier of the SIM-card - IMSI (International Mobile Subscriber Identity). Hard to believe, but it's really a small device, which can imitate a cell tower. GSM network standard provides for mandatory device authentication in the network within the absence of such a commitment from the network itself. Trap disables encryption, collects data and transmits already decrypted signal to the base station (A trap, of course cannot connect the subscriber).
Insecure access to the Wi-Fi network or imitation points are also a way to intercept the traffic in radio channel. Scams use special sniffers (traffic analyzers), which receive information from the wireless adapter and decodes the data. Today devices with NFC became incredibly popular. NFC are wireless modules of high-frequency network of short-range, acting at a distance up to 20 cm. The technology is widespread in access control systems and payment systems, built into many tablets and smartphones. This technology can be connected with the phone hacking in the immediate proximity.
And of course, no one has canceled one of the most dangerous threats pattern in the GSM network - forgotten, lost and stolen phones. Regardless how you have encrypted or how many passwords you have set there is always a program that can get access to your data. Employees of Tottoli GSM can give you only one piece of advice - do not store important personal and business information in your phone and don’t log from your phone to important cloud services, if you use any.
Subscriber network GSM - a combination of specific identifiers of a SIM-card and mobile device. SIM-card - is the cornerstone of privacy in GSM networks. On its microcontroller it keeps individual user’s information, encryption software, keys.
For mobile device the primary identifier is IMEI (International Mobile Equipment Identity). Roughly speaking, this is the serial number that is unique to the device and stored in it. Knowing IMEI it is possible to search for a stolen phone, check its origin, and prohibit access to the equipment for security reasons. In addition, the opportunities of IMEI help to prevent fraud and criminal access. This parameter is passed to the network. The subscriber’s identifier is IMEI (International Mobile Subscriber Identity). This parameter is passed to the network. This is the identifier is written in the SIM, turns the phone in a mobile terminal that identifies the subscriber, registers his in a roaming and is used for billing.
Public parameter MSISDN - (Mobile Subscriber Integrated Services Digital Number) - number of the mobile subscriber digital network with integrated services for communication in standard GSM, UMTS and so on. It is dialed when a subscriber makes a call. This option is not passed to the network, but is comparable to the IMSI.
These parameters are enough to get all necessary information and to use it for analytical conclusions. Gaining these identifiers by means of LESS, intercept complexes and other mechanisms it is possible to get the following information about a subscriber:
It is time return to the discussion of the special SIM-cards, which can protect the subscriber from potential threats, which is especially valuable for the corporate network
Models of threats were described above. Now we would like to outline how our technology minimize these threats.
- We use several profiles on the same SIM card, with the ability to produce rotation of the profile by the air (OTA). (To clarify: the profile is a set of identifiers (IMSI + KI)).
- We do not use public identifier MSISDN, we use a DID-number, or FMC-numbers within network.
- The BTS (base station) selection procedure does not allow to use standard algorithms for cell selection. We use our algorithms as much as our capabilities allow. This mechanism is designed to evade interception complexes. We use a variety of telltale factors of interception, SIM card applet and the mechanism of interaction of the SIM-card and our server for the required calculations. Based on the findings of our work, we do not allow SIM card to work with a tower that raises suspicions.
- Within Tottoli GSM platform personalized billing from operators is absent.
Let’s consider some specific examples of realization of threat protection within Tottoli-GSM technology.
A subscriber with a usual SIM-card after number dialing presses the Call-button. At this stage, a mobile device sends ALERT signal via FACCH (Fast Associated Control Channel) to the BSS (Base Station Subsystem). Then this signal goes to MSC (Mobile Switching Center). MSC sends Address Complete message to the calling subscriber (the party that originates the call). The subscriber who made a call hears the dial tone, and the called party hears ringing sound. If the number (MSISDN) of one of the subscribers is known, it is possible to get all the call details from the operator’s billing and the session itself. Also it is possible to intercept the session over the air by technical means.
Tottoli GSM user after number dialing presses the Call-button. At this stage, the call is aborted. At the same time the encrypted command is sent through the signal channel to the Tottoli GSM SECURITY server ATS (Automatic Telephone Station). Tottoli GSM’s ATS through SS7 requests VLR (Visitor Location Register) for a temporary number – MSRN (Mobile Station Roaming Number) – for this particular SIM and this particular call. As soon as the operator has allocated MSRN to a SIM, Tottoli GSM ATS starts calling this number. At this stage the call to Tottoli GSM starts. When the Tottoli GSM subscriber answers this call, the first leg opens. Then Tottoli GSM ATS starts calling the second party. When the second party answers the call, the second leg opens (Call Back technology).
Using this mechanism for call making it is not possible to get the information from the operator’s billing, as it is unknown what operator Tottoli GSM SIM is registered to, and as a result there is no public identifier - MSISDN by means of which IMSI, Ki and IMEI parameters are obtained. Even if the second subscriber is under control it is impossible to understand who he’s had a conversation with, as the session consists of two legs, and both legs are separated by AY server ATS, and as a result it is not possible to define the circle of your contacts.
A call to a usual SIM-card is performed according to the standard procedures. After the performance of call procedure and TMSI assignment (Temporary Mobile Subscriber Identity) in the VLR coverage area, traffic is terminated and the session is considered as set-up. The operator’s billing records the information about the device that originates the call, the location of the call accepting device during the session, call duration, etc.
A call to Tottoli GSM is performed in a following way: a virtual number - DID is assigned to Tottoli GSM SIM. DID number accepts call from a network, changes it into SIP protocol and routes it to Tottoli GSM ATS. Tottoli GSM ATS, in its turn, defines a subscriber who this DID belongs to, and starts the call procedure described above. Thus, it is not possible to locate Tottoli GSM SIM and to detect a connection between both subscribers, as Tottoli GSM ATS stands in – between.
Considering the fact that mobile operators actively introduce into their networks mechanisms of subscriber searching by phonetic characteristics (voice print), Tottoli GSM allows to change the acoustic characteristics of your voice for inbound and outbound calls. This mechanism is especially useful if the call from Tottoli GSM is made on a usual SIM.
Perhaps each of us has the information we want to protect. When it comes to the private sphere, disseminating this information entails various risks, which are rarely serious for the owner. When it comes to corporate data, the risk of loss or compromise it can cost a lot. If you have something to lose, it is worth thinking about how to save it, also with the help of Tottoli GSM. Hunters for valuable information don’t sleep.

